How Legacy Modernization in Banks Prevents Outages During Peak Loads?
Legacy modernization in banks boosts scalability, prevents outages, strengthens resilience, and ensures uninterrupted peak-hour performance.
Read Story


This blog is your go-to guide for implementing Single Sign-On (SSO) in Django applications using SAML and Microsoft Azure Active Directory. Learn the step-by-step process, from Azure AD app registration to user authentication and JWT token generation. Elevate user experience and security by seamlessly integrating your Django app with Azure AD for efficient and secure authentication.
Single Sign-On (SSO) is an authentication process that allows users to access multiple applications with a single set of login credentials. Instead of maintaining separate login credentials for each application, users authenticate once and gain access to all connected services seamlessly.
Create an Azure AD App: An Azure AD App represents your Django application in the Azure Active Directory. It serves as a bridge between your app and the Identity Provider (IdP). During registration, you obtain an "Application (client) ID" and "Directory (tenant) ID."
Configure Redirect URI: Specify the Redirect URI, where Azure AD will send the SAML response after successful authentication. This should be a route in your Django app,
Generate Client Secret: A client secret is a secure key that the Django app uses to authenticate with Azure AD. Generate a new client secret, and keep it secure.
Add API Permissions:
Grant Admin Consent:
Why Use a Certificate and Metadata XML?
A certificate is used to sign and encrypt SAML messages exchanged between the Service Provider (Django) and the Identity Provider (Azure AD). The metadata XML file contains crucial information about your app's SAML configuration, making it easier to set up the IdP.
Generating a Self-Signed Certificate: Use OpenSSL to generate a self-signed certificate consisting of a private key, public key, and a combined PKCS#12 certificate file.
Download Azure AD Metadata XML:
Install DjangoSAML2: djangoSAML2 is a Django package that simplifies the integration of SAML-based SSO. Install it using pip:

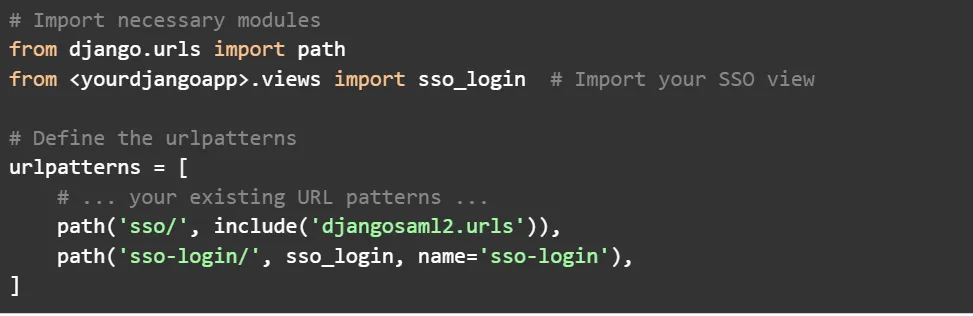
Configure DjangoSAML2: In your Django project settings, configure djangoSAML2 with the necessary parameters. This includes details about your app as well as Azure AD's SAML configuration.
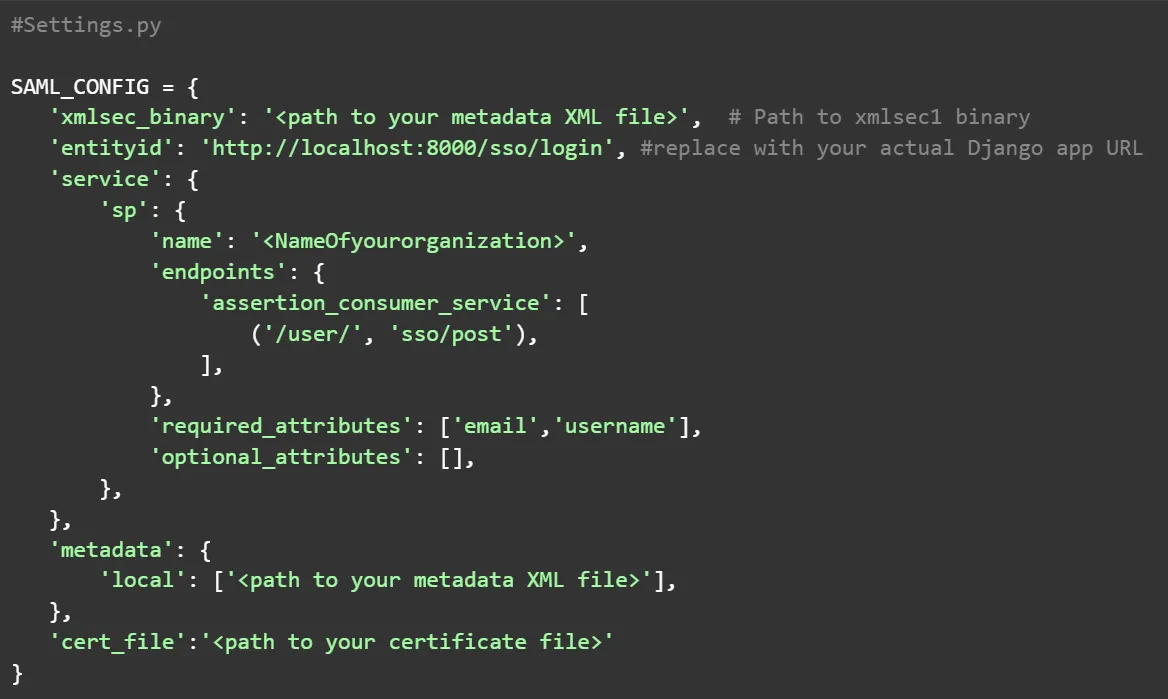
Implement SSO View: Create a Django view that will handle the SAML response from Azure AD. This view initializes the OneLogin_Saml2_Auth object, processes the response, and extracts user information from the SAML assertion.
Extracting User Attributes: Use the get_attribute method to extract relevant user attributes such as username and email from the SAML assertion.
Implement SSO View:
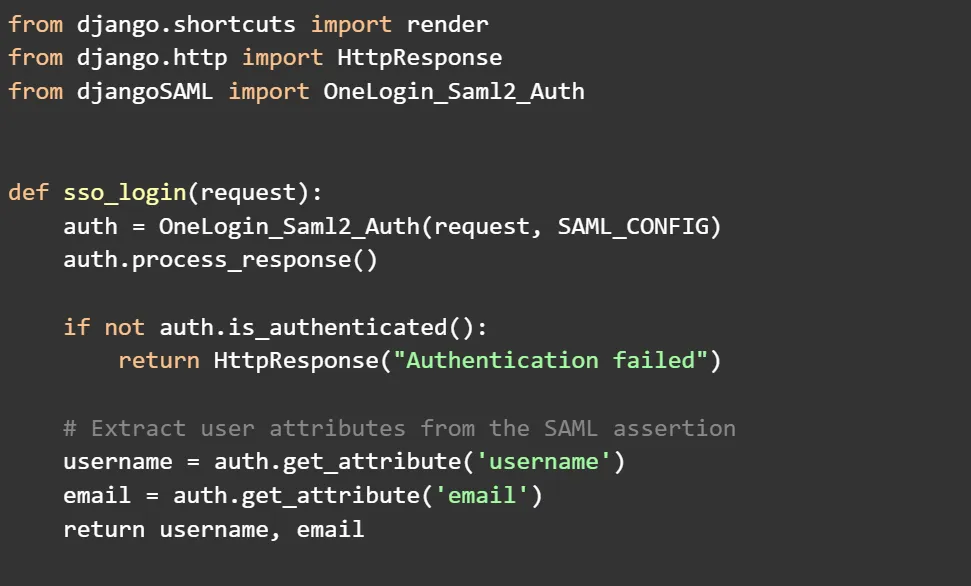
Generate JWT Tokens: Utilize Django REST Framework and Simple JWT to generate JWT tokens for the authenticated user. This involves creating a user in the Django user table (if not exist) and generating access and refresh tokens.
Why Use JWT Tokens? JWT (JSON Web Tokens) is a secure and efficient way to represent claims between two parties. They are used to authenticate users and grant them access to protected resources.
Generate JWT Tokens:
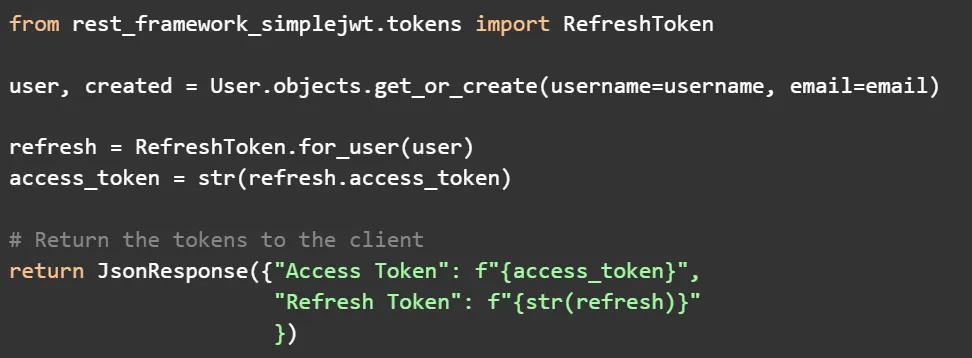
Configuring Django URL Patterns
Open Your Django Project's urls.py file:
Add the DJANGOSAML2 URL Pattern:
Looks too complicated don't worry our experts at Hexaview Tech will help you with top notch Cloud Security Consulting Services.
%201.svg)
%201.svg)
%201.svg)
Helping regulated enterprises modernize systems, adopt AI-first engineering, and deliver outcomes that pass audits the first time.
